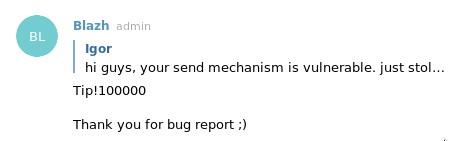
This week I spent coding my very first public pet-app based on Telegram chat bot which acts as a Bitcoin wallet and allows to send and receive tips between Telegram users and other so-called “Lightning Apps”. I assume that you are familiar with Bitcoin & Telegram in general, i’ll try to post short and without deep jump into details. More resources about Bitcoin can be found here and Telegram is simply an instant messenger that allows you to create your custom apps (chat-bots) using their platform.
What are the key points of such app?
- Allows to rate other users ideas and answers with real value instead of
‘virtual likes’. This brings online conversation to completely new level - Real example of working micro-payment app which can act with other entities
over internet using open protocol - All the modules are open-source projects and can be easy re-used and adjusted
for your own project. App does not relay on third-party commercial services.
Even it falls under e-commerce field, which is currently almost closed, the app
is based on open solutions.
What are the use-cases?
something like this…