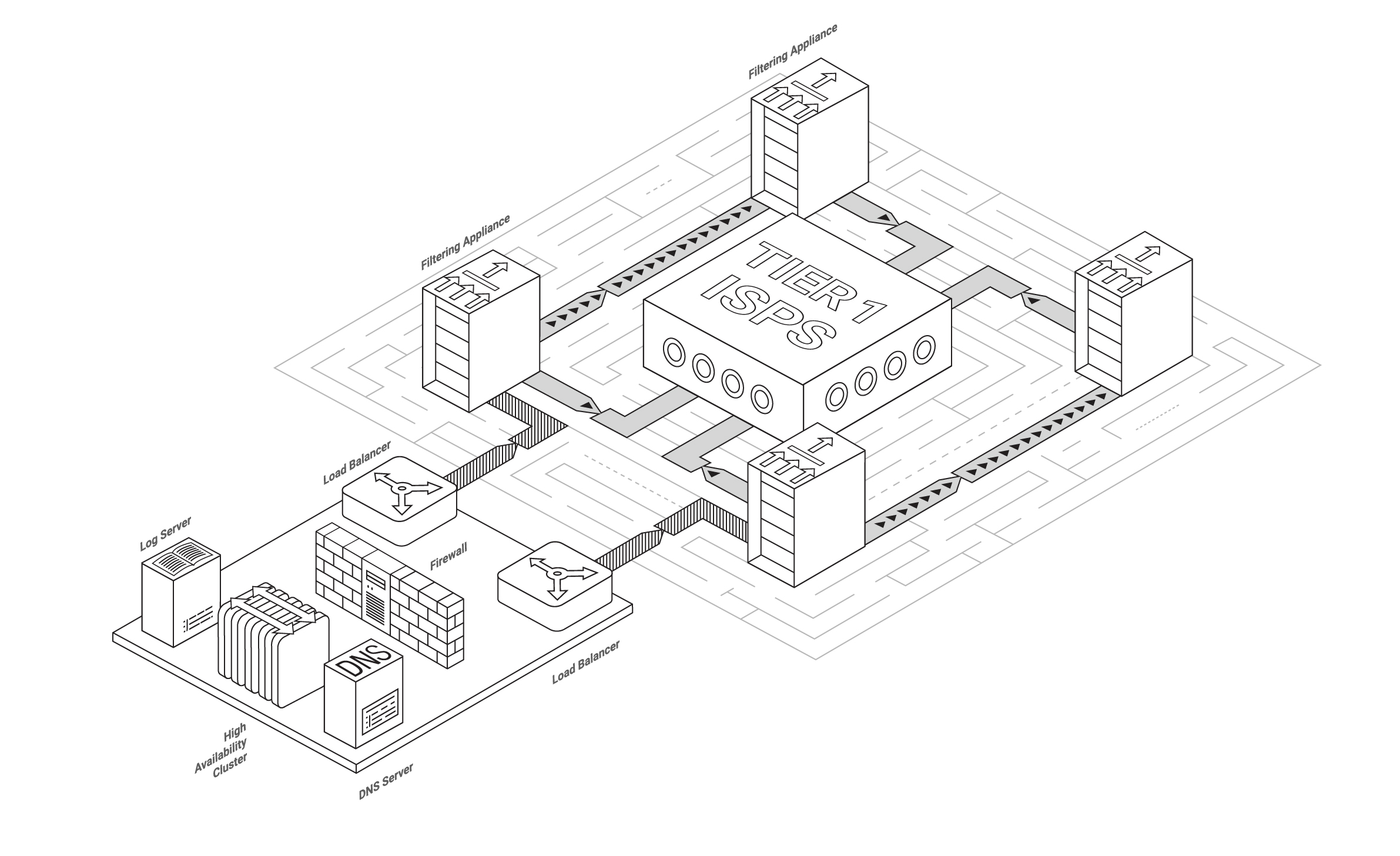
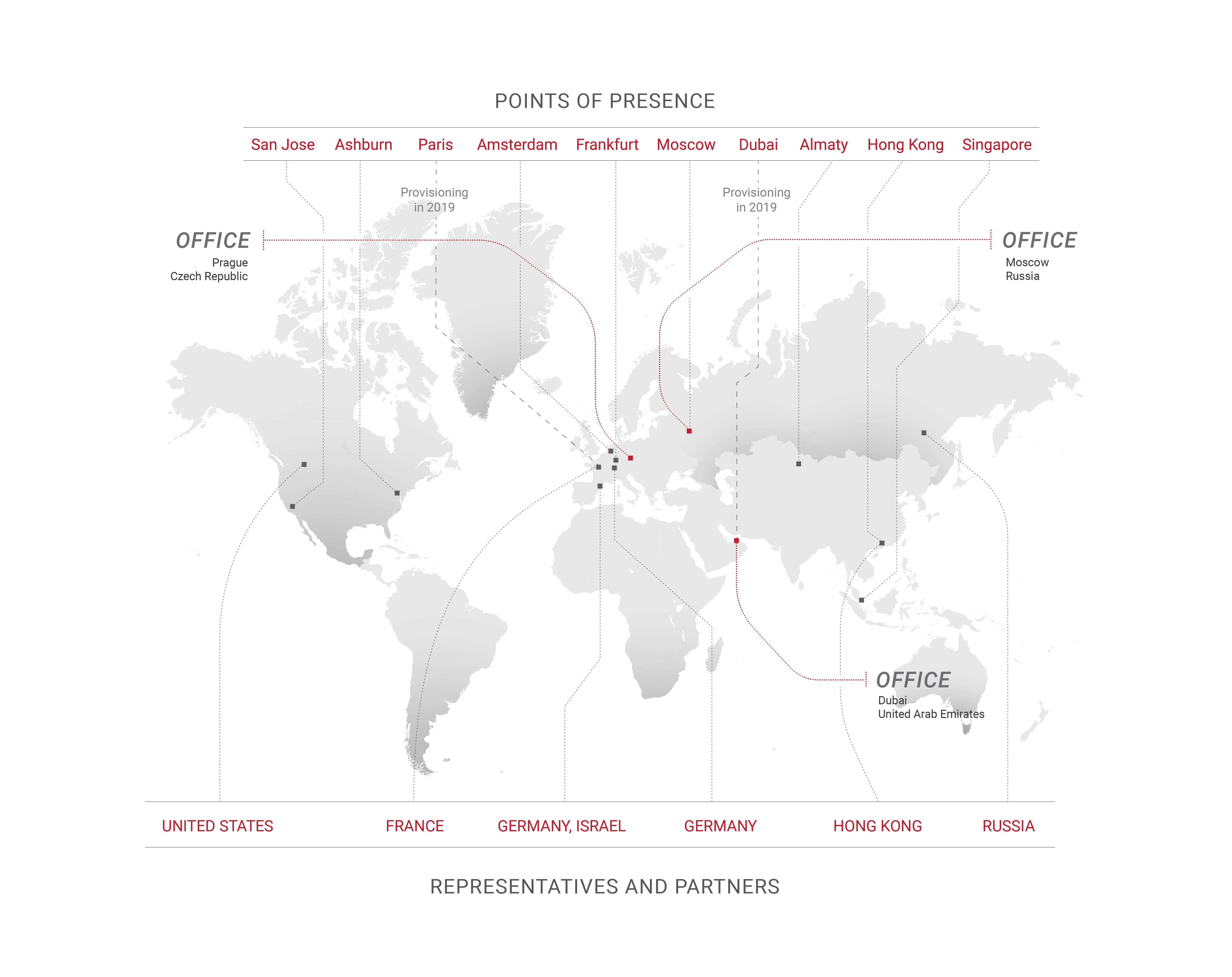
As many of our readers know, Qrator.Radar is constantly researching global BGP connectivity, as well as regional. Since the Internet stands for “Interconnected Networks,” to ensure the best possible quality and speed the interconnectivity of individual networks should be rich and diverse, with their growth motivated on a sound competitive basis.
The fault-resistance of an internet connection in any given region or country is tied to the number of alternate routes between ASes. Though, as we stated before in our Internet Segments Reliability
reports, some paths are obviously more critical compared to the others (for example, the paths to the Tier-1 transit ISPs or autonomous systems hosting authoritative DNS servers), which means that having as many reachable routes as possible is the only viable way to ensure adequate system scalability, stability and robustness.
This time, we are going to have a closer look at the Russian Federation internet segment. There are reasons to keep an eye on that segment: according to the numbers provided by the RIPE database, there are 6183 autonomous systems in Russia, out of 88664 registered worldwide, which stands for 6.87% of total.
This percentage puts Russia on a second place in the world, right after the USA (30.08% of registered ASes) and before Brazil, owning 6.34% of all autonomous systems. Effects of changes in the Russian connectivity could be observed across many other countries dependant on or adjacent to that connectivity, and ultimately by almost any ISP in the world.