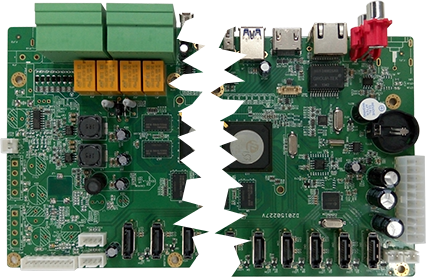
This is a full disclosure of recent backdoor integrated into DVR/NVR devices built on top of HiSilicon SoC with Xiaongmai firmware. Described vulnerability allows attacker to gain root shell access and full control of device. Full disclosure format for this report has been chosen due to lack of trust to vendor. Proof of concept code is presented below.



 Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).
Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).